- Back
- Products
Development Framework & Tools
Qt Framework
Cross-platform software libraries and APIs
Qt Development Tools
Qt Creator IDE and productivity tools
Qt Design Studio
UI Design tool for UI composition
Qt Quality Assurance
for Qt projects
Qt Digital Ads
Digital advertising for UI apps
Qt Insight
Usage intelligence for embedded devices
Quality Assurance Tools
Squish
GUI test automation
Coco
Code coverage analysis
Test Center
Test results management and analysis
Axivion Static Code Analysis
Software static code analysis
Axivion Architecture Verification
Software architecture verification
-
More
Qt 6
The latest version of Qt.
Licensing
Make the most of Qt tools, with options for commercial licensing, subscriptions, or open-source.
Qt Features
Explore Qt features, the Framework essentials, modules, tools & add-ons.
Qt for Python
The project offers PySide6 - the official Python bindings that enhance Python applications.
-
- Solutions
-
Industry & Platform Solutions
Qt empowers productivity across the entire product development lifecycle, from UI design and software development to quality assurance and deployment. Find the solution that best suits your needs.
-
Industry
-
Platform
Automotive
Micro-Mobility Interfaces
Consumer Electronics
Industrial Automation
Medical Devices
Desktop, Mobile & Web
Embedded Devices
MCU (Microcontrollers)
Cloud Solutions
-
More
Next-Gen UX
Insight into the evolution and importance of user-centric trends and strategies.
Limitless Scalability
Learn how to shorten development times, improve user experience, and deploy anywhere.
Productivity
Tips on efficient development, software architecture, and boosting team happiness.
-
- Resources
-
Our Ultimate Collection of Resources
Get the latest resources, check out upcoming events, and see who’s innovating with Qt.
-
Development Framework & Tools
-
Quality Assurance Tools
Qt Resource Center
Qt Blog
Qt Success Stories
Qt Demos
QA Resources
QA Blog
QA Success Stories
-
- Learn
-
Take Learning Qt to the Next Level
A wealth of Qt knowledge at your fingertips—discover your ideal learning resource or engage with the community.
-
Learn with us
Qt Academy
Qt Educational License
Qt Documentation
Qt Forum
-
- Support
-
We're Here for You—Support and Services
Whether you're a beginner or a seasoned Qt pro, we have all the help and support you need to succeed.
-
Available now: MISRA C++:2023 and MISRA C:2023 check! Read more

Axivion Suite:
Static Code Analysis & Architecture Verification
Through acquisition the Qt Group can now offer you industry-leading tools for static code analysis and software architecture verification. Combining Axivion Static Code Analysis and Axivion Architecture Verification will give you a holistic, in-depth analysis of your code.
If you are interested in receiving more information or would like to discuss the possibility of an evaluation, please contact us.
Strive for Quality, Inspired by Our Customers










































Axivion Suite – A Holistic Solution to Assure the Quality of Your Software
Combining Axivion Static Code Analysis and Axivion Architecture Verification gives you a powerful set of tools to ensure your software code meets the high standards your customers expect from you. Axivion Suite helps you to identify software erosion (also known as technical debt) or to avoid it from the outset in order to keep your software project maintainable and scalable in future.
If your are developing software in safety-oriented environments, the Axivion Tool Qualification Kit gives you the additional support to achieve the tool confidence level (TCL) you require.
Scalable static code analysis with abstract interpretation and pointer analysis
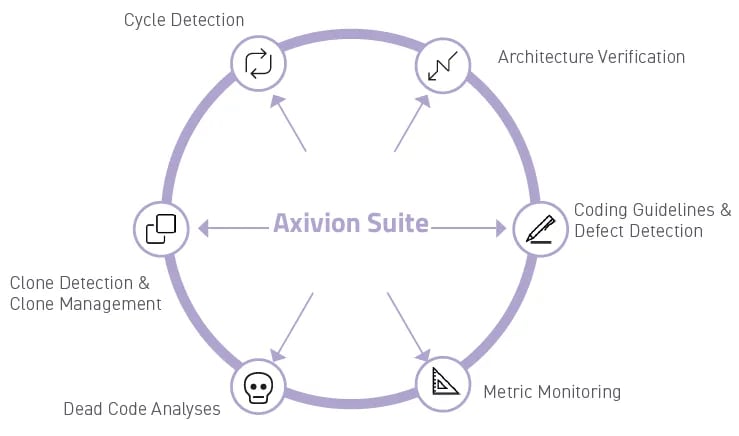
Axivion Suite - Key Features
Whether you want all features at once or prefer to start with just some of them - you can always rely on hassle-free integration into your existing development environment.
Contact us to learn how we can support your individual use case.
Axivion Static Code Analysis
Axivion Static Code Analysis checks software projects for style and coding violations. Detecting clones, dead code, division by zero and other defects in the code at an early stage reduces the time and costs involved in fixing these issues at a later stage.
Axivion Architecture Verification
Implementing Axivion Architecture Verification ensures that the system’s structure remains clear and clean. To create the structural model of your software architecture, you can either set it up manually or import it from a UML model or from any other form of graph structure.
Coding Guidelines
With Axivion Suite’s automatic coding guidelines checkers, risky vulnerabilities in the code are easily found during development. The integrated delta analysis enables targeted reactions to newly emerging risks in the code.
Metrics
Benefit from included rule sets for common software metrics. These includes metrics based on lines and tokens, nesting, cyclomatic complexity, control flow or golden oldies like Halstead metrics. Even whole rule sets like HIS are supported.
Defect Analysis
The defect analysis checks the source code for potential runtime errors. It includes scalable data and control flow checks. These allow errors such as out-of-bounds access or division by zero to be detected at an early phase of the software development.
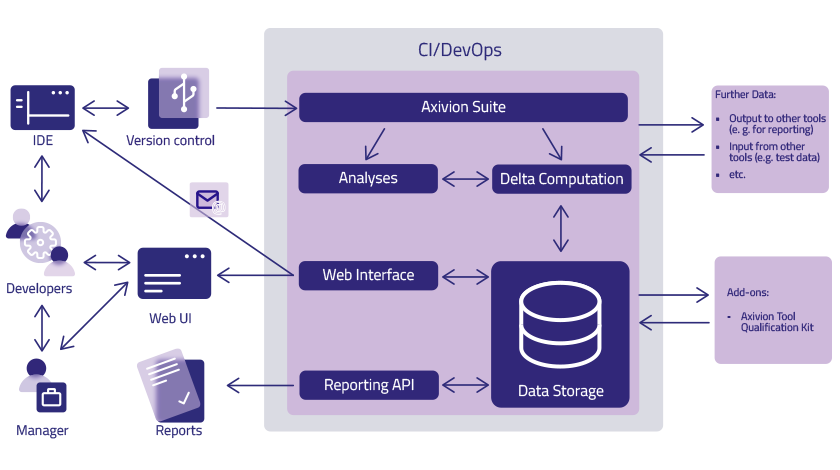
Axivion Tool Qualification Kit
The Axivion Tool Qualification Kit is the perfect add-on to support classification and qualification of your tool chain. This comprises prefabricated test suites with execution and results evaluation processes that can be automated.
Our Versatile Tools Seamlessly Integrate Into Your Development Environment
The Axivion Static Code Analysis and Axivion Architecture Verification seamlessly integrate into your existing development environment. The tools are highly customizable and adapt to your individual needs. Our experts will support the entire roll-out process to ensure you can enjoy the benefits right from the start.
Automated quality assurance which reduces defects, code footprint and dependency on individuals
Holistic and comprehensive analysis for increased productivity and ROI by saving time, money and resources
Fully customizable and easy to integrate into your existing development environments
Scalable tool, which adapts to changing requirements and grows with your needs
Follows industry-leading safety & security standards to ensure your code is compliant
Targeted review with detailed delta-analysis as part of the CI process e.g. before code is committed or to monitor improvements and prevent software erosion
Helps ensuring cyber security by checking code compliance with CERT, CWE and other security guidelines
On-time delivery of feature releases of your software thanks to risk mitigation
Unmatched service and support to ensure you benefit right from the start, e.g. support during roll-out
Success Stories for Axivion Suite from Various Industries
Visit our QA Resource Center for more Success Stories
Apex.AI
Assured with Axivion
“We have evaluated several static analysis tools, and Axivion Suite clearly stood out in our tests. The tool performed best in terms of AUTOSAR C++14 coverage and convinced us through its ease of use, control flow, and data flow analysis, and report generation. Axivion Suite has already become a mainstay component in our development workflow and a valuable component of our DevOps pipeline.”
Dejan Pangercic
CTO and Co-Founder of Apex.AI
Elektrobit
Assured with Axivion
“The Axivion Suite provides us with crucial support when implementing new features in EB street director and guaranteeing the quality of our software solutions in the long term.”
Jakob Schmidt
Software Architect at Elektrobit
Fresenius Medical Care
Assured with Axivion
“Thanks to the Axivion Suite, we have the maintainability of our software under control, thereby safeguarding our long-term capacity for innovation.”
Thomas Stahl
Director Software Engineering at Fresenius Medical Care
HENSOLDT
Assured with Axivion
“With the Axivion Suite, we have significantly reduced our integration effort and integra tion risk.”
Daniel Zimmermann
Head of OSS Software at HENSOLDT Sensors GmbH
Stopping Software Erosion
Coming soonDownload the Brochure
DownloadRequest a Demo
Contact UsQt Quality Assurance
Explore our entire Product PortfolioQuality Assurance for Industrial Solutions
Read MoreQt Group includes The Qt Company Oy and its global subsidiaries and affiliates.
